Cisco Cloud Security: Protecting Your Business in the Cloud
As businesses increasingly move their data and operations to the cloud, cloud security has become a critical concern. The cloud offers many benefits, such as increased flexibility, scalability, and cost savings. However, it also presents new security challenges that must be addressed in order to ensure the safety of sensitive data and systems.
Cisco is a leader in cloud security solutions, offering a comprehensive suite of products and services designed to protect businesses in the cloud. Cisco’s cloud security solutions provide end-to-end protection for all types of cloud environments, including public, private, and hybrid clouds.
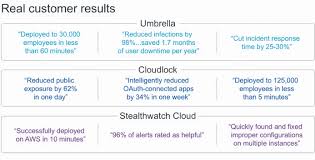
One of Cisco’s key offerings in this area is Cisco Umbrella. Umbrella is a cloud-based security platform that provides protection against threats such as malware, phishing attacks, and ransomware. It uses machine learning algorithms to identify threats in real-time and block them before they can do any damage.
Another important product in Cisco’s cloud security portfolio is Cisco Cloudlock. Cloudlock provides visibility into all cloud applications being used by an organization and helps identify potential risks or compliance violations. It also provides data loss prevention (DLP) capabilities to prevent sensitive data from being shared or leaked.
Cisco also offers a range of other products and services to enhance cloud security, such as firewalls, intrusion prevention systems (IPS), and secure web gateways (SWG). These products are designed to work together seamlessly to provide comprehensive protection for businesses operating in the cloud.
In addition to its product offerings, Cisco has also developed best practices for securing the cloud that can help businesses navigate the complex landscape of cloud security. These best practices include implementing strong authentication mechanisms, encrypting data both at rest and in transit, regularly monitoring for vulnerabilities or threats, and maintaining compliance with relevant regulations.
In conclusion, as more businesses move their operations to the cloud, it is essential that they prioritize their security needs. Cisco’s comprehensive suite of products and services, combined with their industry-leading expertise in cloud security, make them a top choice for businesses looking to protect their data and systems in the cloud. By implementing best practices and leveraging Cisco’s cloud security solutions, businesses can enjoy the many benefits of the cloud while also maintaining a strong security posture.
6 Essential Tips for Securing Your Cisco Cloud Environment
- Make sure to use the latest version of Cisco Cloud Security software, as it will have the most up-to-date security features.
- Utilize two-factor authentication and strong passwords to protect your data and accounts from unauthorized access.
- Implement segmentation controls within your cloud environment to limit potential attack vectors.
- Monitor user activity regularly for suspicious behavior or unusual activities that could indicate a breach in security.
- Set up alerts and notifications so you are immediately aware of any security threats or breaches in your system.
- Train employees on best practices for cybersecurity, such as avoiding phishing scams and using secure networks when accessing sensitive data remotely
Make sure to use the latest version of Cisco Cloud Security software, as it will have the most up-to-date security features.
When it comes to cloud security, it’s essential to stay up-to-date with the latest software versions and security features. This is particularly true for Cisco Cloud Security, which offers a range of products and services designed to protect businesses in the cloud.
One important tip for ensuring the security of your cloud environment is to make sure you are using the latest version of Cisco Cloud Security software. This will ensure that you have access to the most up-to-date security features and protections against emerging threats.
By staying current with the latest software updates, you can take advantage of new security technologies and capabilities that can help keep your data safe. These updates may include patches for vulnerabilities or new threat detection algorithms that can identify and block malicious activity in real-time.
In addition to keeping your software up-to-date, it’s also important to regularly monitor your cloud environment for potential threats or vulnerabilities. This can help you identify and address security issues before they become major problems.
Overall, by following best practices for cloud security and using the latest version of Cisco Cloud Security software, businesses can enjoy the many benefits of the cloud while also maintaining a strong security posture. So make sure to prioritize software updates and regular monitoring as part of your overall cloud security strategy.
Utilize two-factor authentication and strong passwords to protect your data and accounts from unauthorized access.
Two-Factor Authentication and Strong Passwords: Essential Tips for Cisco Cloud Security
As businesses increasingly move their operations to the cloud, security has become a top concern. The cloud offers many benefits, but it also presents new security challenges that must be addressed in order to protect sensitive data and systems. One of the most important steps that businesses can take to enhance their cloud security is to utilize two-factor authentication and strong passwords.
Two-factor authentication adds an extra layer of security beyond just a password. With two-factor authentication, users must provide two forms of identification before they can access their accounts or data. This could be something like a password and a fingerprint scan, or a password and a code sent to their phone. By requiring two forms of identification, businesses can ensure that only authorized users are able to access their data and accounts.
In addition to utilizing two-factor authentication, it is also essential to use strong passwords. A strong password should be at least 12 characters long and include a mix of letters, numbers, and symbols. It should not include any easily guessable information such as names or dates that are associated with the user. By using strong passwords, businesses can make it much more difficult for hackers or unauthorized users to gain access to their data.
Cisco offers many tools and solutions for enhancing cloud security, but utilizing two-factor authentication and strong passwords is one of the simplest yet most effective steps that businesses can take on their own. By implementing these best practices, businesses can significantly reduce the risk of unauthorized access to their data and accounts in the cloud.
In conclusion, as more businesses move their operations to the cloud, it is essential that they prioritize their security needs. Utilizing two-factor authentication and strong passwords is an essential step towards protecting sensitive data in the cloud. By following these best practices alongside other Cisco cloud security solutions, businesses can enjoy the many benefits of the cloud while maintaining a strong security posture.
Implement segmentation controls within your cloud environment to limit potential attack vectors.
Implementing Segmentation Controls in Your Cloud Environment for Enhanced Cisco Cloud Security
As businesses increasingly move their operations to the cloud, cloud security has become a major concern. One important tip for enhancing Cisco cloud security is to implement segmentation controls within your cloud environment. This can help limit potential attack vectors and protect sensitive data.
Segmentation controls involve dividing your cloud environment into smaller, more manageable segments or zones. By doing this, you can better control access to different parts of your environment and limit the potential impact of a security breach.
For example, you might segment your environment based on user roles or types of data being stored. This can help ensure that users only have access to the data they need to do their jobs and limit the potential for unauthorized access.
Implementing segmentation controls can also help with compliance requirements by ensuring that sensitive data is properly protected and only accessible by authorized personnel.
There are several tools available from Cisco that can help with implementing segmentation controls in your cloud environment. For example, Cisco’s Application Centric Infrastructure (ACI) provides a comprehensive approach to network segmentation that allows you to create policies based on business requirements.
In conclusion, implementing segmentation controls within your cloud environment is an important step towards enhancing Cisco cloud security. By dividing your environment into smaller segments and controlling access to different parts of it, you can limit potential attack vectors and protect sensitive data. With the right tools from Cisco, such as ACI, implementing these controls can be easier than ever before.
Monitor user activity regularly for suspicious behavior or unusual activities that could indicate a breach in security.
Cisco Cloud Security Tip: Monitor User Activity Regularly to Stay Ahead of Breaches
As businesses increasingly move their operations to the cloud, it is important to stay vigilant about potential security threats. One key way to do this is by monitoring user activity regularly for any suspicious behavior or unusual activities that could indicate a breach in security.
User activity monitoring involves keeping track of all user actions within the cloud environment, including logins, file transfers, and changes to system configurations. By monitoring user activity, businesses can quickly identify any unusual or suspicious behavior that could indicate a security breach.
For example, if a user logs in from an unfamiliar location or attempts to access files they are not authorized to access, this could be a red flag. By catching these types of activities early on, businesses can take steps to prevent further damage and protect their sensitive data.
Cisco offers several tools and solutions that can help businesses monitor user activity in the cloud. For example, Cisco Cloudlock provides real-time visibility into all cloud applications being used by an organization and helps identify potential risks or compliance violations. It also provides data loss prevention (DLP) capabilities to prevent sensitive data from being shared or leaked.
In addition to using these tools and solutions, it is important for businesses to establish clear policies and procedures around user activity monitoring. This includes defining what types of activities are considered suspicious and how they will be investigated.
In conclusion, staying ahead of potential security breaches requires constant vigilance and proactive measures. By regularly monitoring user activity in the cloud environment and taking swift action when necessary, businesses can protect their sensitive data and systems from harm. With Cisco’s comprehensive suite of cloud security solutions and best practices in place, businesses can stay one step ahead of potential threats and enjoy the many benefits of the cloud with confidence.
Set up alerts and notifications so you are immediately aware of any security threats or breaches in your system.
Cisco Cloud Security Tip: Set Up Alerts and Notifications for Immediate Awareness of Threats
In today’s digital landscape, security threats are constantly evolving and becoming more sophisticated. As businesses move their operations to the cloud, it is essential that they prioritize their security needs and take steps to protect their data and systems.
One important step in securing your cloud environment is to set up alerts and notifications so that you are immediately aware of any security threats or breaches in your system. By doing so, you can take swift action to mitigate the impact of any potential attacks.
Cisco offers a range of products and services designed to help businesses monitor their cloud environments and detect security threats. For example, Cisco Umbrella provides real-time threat intelligence and alerts on potential threats such as malware, phishing attacks, or ransomware. Similarly, Cisco Cloudlock provides visibility into all cloud applications being used by an organization and alerts on potential risks or compliance violations.
By setting up alerts and notifications through these tools, businesses can stay ahead of potential threats and take proactive measures to protect their data and systems. This includes implementing additional security measures such as firewalls or intrusion prevention systems (IPS) to prevent future attacks.
In conclusion, setting up alerts and notifications is a critical step in securing your cloud environment. By leveraging Cisco’s suite of cloud security products and services, businesses can stay ahead of potential threats and take swift action to mitigate any impact. Don’t wait until it’s too late – set up alerts today!
Train employees on best practices for cybersecurity, such as avoiding phishing scams and using secure networks when accessing sensitive data remotely
One of the most important tips for maintaining strong cloud security is to train employees on best practices for cybersecurity. This includes educating them on how to avoid phishing scams and use secure networks when accessing sensitive data remotely.
Phishing scams are a common tactic used by cybercriminals to trick employees into divulging sensitive information or clicking on malicious links. By training employees on how to identify and avoid these scams, businesses can greatly reduce the risk of a data breach or cyberattack.
In addition, when employees access sensitive data remotely, it is important that they do so using a secure network. This means using a virtual private network (VPN) or other secure connection to ensure that data is encrypted and protected from prying eyes.
By implementing these best practices and training employees on how to follow them, businesses can greatly enhance their cloud security posture. In addition, regular training and education can help keep employees up-to-date on the latest threats and vulnerabilities, ensuring that they are able to quickly identify and respond to potential security incidents.
Overall, employee education is an essential component of any effective cloud security strategy. By investing in training and education programs, businesses can help mitigate the risk of cyberattacks and protect their sensitive data in the cloud.
Tags: benefits, business, cisco, cisco cloud security, cloud environments, cloud security, comprehensive suite of products and services, cost savings, critical concern, data, end-to-end protection, flexibility, leader, operations, private clouds hybrid clouds, public clouds, scalability, security challenges, sensitive data, solutions, systems