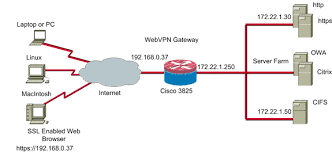
Cisco SSL VPN is a secure and reliable virtual private network (VPN) solution that provides remote access to corporate networks, applications, and resources. It enables users to securely access their organization’s network from any device with an Internet connection.
Cisco SSL VPN technology is based on the industry-standard Secure Sockets Layer (SSL) protocol, which provides strong encryption and authentication for secure remote access. It also supports various authentication methods, such as digital certificates and two-factor authentication. This makes it an ideal solution for organizations that need to protect their sensitive data while allowing their employees to work remotely.
The Cisco SSL VPN solution is easy to deploy and manage, with a single unified client that works across multiple platforms including Windows, Mac OS X, Linux, iOS, and Android. It also supports multiple devices per user account so that users can securely access their organization’s network from any of their devices.
The Cisco SSL VPN solution also offers several advanced features such as granular access control lists (ACLs), which allow administrators to specify which resources are available to each user or group of users; split tunneling which allows users to have direct access to the Internet while still being connected to the corporate network; and clientless web-based access for users who don’t have the Cisco AnyConnect client installed on their device.
Overall, Cisco SSL VPN is a powerful and secure enterprise-grade solution that provides organizations with a secure remote access solution for their employees while protecting their sensitive data.
7 Tips for Using Cisco SSL VPN
- Use the latest version of Cisco AnyConnect for the best security and performance.
- Enable two-factor authentication to add an extra layer of security to your VPN connection.
- Utilize strong passwords and change them regularly to minimize risk of unauthorized access.
- Configure your firewall settings properly to ensure that only authorized users are able to access the VPN network resources.
- Make sure you have adequate anti-virus and malware protection on all devices connected to the VPN network, as well as up-to-date patches applied for any software installed on these devices.
- Implement a policy regarding acceptable use of company resources over the SSL VPN, including restrictions on downloading or uploading data from external sources without prior authorization from IT personnel or management personnel with appropriate privileges
- Monitor user activity regularly and investigate any suspicious activities immediately
Use the latest version of Cisco AnyConnect for the best security and performance.
Cisco AnyConnect is a secure, reliable and easy-to-use VPN solution that provides secure remote access to corporate networks, enabling users to access their files, applications, and desktops from anywhere. It is a powerful tool for businesses that need to provide secure remote access for their employees.
The latest version of Cisco AnyConnect offers the best security and performance for businesses. It includes improved encryption algorithms and stronger authentication protocols that help protect against data breaches. Additionally, the latest version of Cisco AnyConnect provides faster connection speeds, allowing users to access their resources quickly and efficiently.
Cisco AnyConnect also offers enhanced user experience with its intuitive interface and easy setup process. The software can be easily installed on any device, including Windows, MacOS, iOS and Android devices. Furthermore, it offers advanced features such as split tunneling which allows users to route specific traffic through the VPN while other traffic goes through the local connection.
Overall, businesses should consider upgrading to the latest version of Cisco AnyConnect in order to ensure maximum security and performance for their remote access needs.
Enable two-factor authentication to add an extra layer of security to your VPN connection.
Two-factor authentication (2FA) is a powerful way to secure your Cisco SSL VPN connection. By enabling 2FA, you add an extra layer of security to your VPN connection, making it much harder for malicious actors to gain access to your network.
2FA works by requiring users to provide two pieces of information before they can access the VPN. The first is a traditional username and password combination. The second is a unique code generated by an authentication app or sent via text message or email. This second factor makes it far more difficult for attackers to gain access, as they would need both the username and password as well as the one-time code generated by the authentication app or sent via SMS or email.
Enabling 2FA on your Cisco SSL VPN is easy and can be done in just a few steps. All you need to do is create a user account in the Cisco AnyConnect Security Mobility Client, enable two-factor authentication in the settings, and then configure the authentication app or SMS/email delivery method for each user account. Once this is done, users will be required to provide both their username and password as well as the unique code generated by their authentication app or sent via SMS/email before they can access the VPN.
By enabling 2FA on your Cisco SSL VPN, you can rest assured that your network is secure from malicious actors attempting to gain unauthorized access.
Utilize strong passwords and change them regularly to minimize risk of unauthorized access.
Secure access to corporate networks is essential for businesses of all sizes. To ensure that only authorized users can gain access, companies often utilize secure socket layer (SSL) virtual private networks (VPN). These networks require users to enter a username and password to gain access. To maximize security, it is important for companies to utilize strong passwords and change them regularly.
Strong passwords are those that are long and contain a combination of numbers, letters, and symbols. By using strong passwords, companies can minimize the risk of unauthorized access by hackers or malicious actors. It is also important for companies to regularly change their passwords to further reduce the risk of unauthorized access.
By utilizing strong passwords and changing them regularly, businesses can better protect their corporate networks from unauthorized access. This will help protect sensitive data from being compromised and help maintain the trust between customers and the business. Companies should also consider implementing other security measures such as two-factor authentication or biometric authentication to further protect their networks.
Configure your firewall settings properly to ensure that only authorized users are able to access the VPN network resources.
Secure access to your network resources is essential for any business, and the best way to ensure that only authorized users can access your VPN network is by properly configuring your firewall settings. Firewalls are an important part of any security system, and they can help protect your network from malicious attacks and unauthorized access.
When configuring your firewall settings for a Cisco SSL VPN, it is important to ensure that only authorized users are able to access the network resources. This means setting up user authentication so that only those with the correct credentials are able to log in. Additionally, you should also configure the firewall to block certain types of traffic from entering or leaving the network. This will help prevent unauthorized users from accessing sensitive data or applications on your network.
Another important step in securing your Cisco SSL VPN is to enable logging and monitoring of all activity on the network. This will allow you to track any suspicious activity or attempts at unauthorized access. It will also give you an additional layer of protection in case a malicious user manages to bypass your authentication measures.
By properly configuring your firewall settings, you can ensure that only authorized users are able to access the resources on your VPN network. This will help keep your data secure and protect it from malicious attacks or unauthorized access.
Make sure you have adequate anti-virus and malware protection on all devices connected to the VPN network, as well as up-to-date patches applied for any software installed on these devices.
In today’s world, cyber security is an increasingly important aspect of any organization’s operations. With the rise of remote working, it is essential for companies to ensure that their data and networks are properly protected against malicious actors. One way to do this is by using a secure SSL VPN connection. However, it is not enough to simply have a secure connection; it is also important to make sure that all devices connected to the VPN network have adequate anti-virus and malware protection, as well as up-to-date patches applied for any software installed on these devices.
Having up-to-date anti-virus and malware protection on all devices connected to the VPN network will help protect against malicious actors who may be attempting to gain access to the network. Additionally, regularly applying patches for any software installed on these devices will ensure that any potential vulnerabilities in the software are addressed before they can be exploited by hackers.
By taking these steps, organizations can ensure that their data and networks remain secure even when accessed remotely via a VPN connection. This will help protect against malicious actors who may be attempting to gain access to sensitive information or cause disruption through malicious activities.
Implement a policy regarding acceptable use of company resources over the SSL VPN, including restrictions on downloading or uploading data from external sources without prior authorization from IT personnel or management personnel with appropriate privileges
In today’s world, the need for secure access to company resources is of paramount importance. To ensure that company resources are used in a secure and responsible manner, it is necessary to implement a policy regarding the acceptable use of company resources over the Cisco SSL VPN. This policy should include restrictions on downloading or uploading data from external sources without prior authorization from IT personnel or management personnel with appropriate privileges.
This is important for two reasons. Firstly, it ensures that any data downloaded or uploaded from external sources is done so securely and responsibly, reducing the risk of malicious software or data being introduced into the network. Secondly, it ensures that only authorized personnel are able to access sensitive information, reducing the risk of unauthorized access and potential misuse of company resources.
By implementing such a policy, companies can ensure that their resources are used in a secure and responsible manner while also protecting their networks from malicious software or unauthorized access.
Monitor user activity regularly and investigate any suspicious activities immediately
Cisco SSL VPNs are a secure and reliable way to provide remote access to your network, but it is important to remember that security is always an ongoing process. To ensure the safety of your network and the data stored within it, regular monitoring of user activity should be part of your security protocol. This means keeping an eye out for any suspicious activities that might indicate malicious intent or unauthorized access attempts. If any such activities are discovered, they should be investigated immediately to ensure that the threat is contained and eliminated.
Monitoring user activity regularly and investigating suspicious activities immediately are essential steps in maintaining a secure environment for your Cisco SSL VPNs. By taking these proactive measures, you can help protect your network from potential threats and keep your data safe.
Tags: android, applications, authentication, cisco anyconnect client, cisco ssl vpn, clientless web-based access, corporate networks, digital certificates, encryption, granular access control lists acls, ios, linux, mac os x, remote access, resources, secure sockets layer, split tunneling, two-factor authentication, windows